What is RFID?
RFID (Radio Frequency Identification) is a technique for reading information on the distance of the transponders and the memories that are called tags.
The cheapest and simplest variants have a very simple structure and consists only of a unique number which they can send out a few inches. This is the most common variety used today. In this type of RFID transponder has all the information stored in a database. Post where information is stored is linked to the unique ID number. This simple type corresponds in fact usual barcodes. The next price tags are a bit more advanced and has an internal memory able to write to several times, but the memory is quite limited. The reader consists of an oscillating magnetic field that induces a sufficient voltage in the antenna of the tag should be able to send their content. The tag can be small enough to fit into a standard price tag, be deployed under the skin of an animal or surgery in humans for identification using radio waves.
How does it work?
Passive tags, RFID
The passive tags have no internal power supply. The tag may be enough power from the reader to send a response. This thanks to the reader antenna by induction creates a sufficient voltage in the tag. The antenna of the passive tags are designed to receive the incoming signal and also send an output signal. The answer from a passive tag is not always just a idnummer but can be more complex, such as information from an integrated memory.
Passive tags have the capacity to be read from 11cm up to 10 meters depending on which standard you use, and also on how the environment looks like. Thanks to the passive tags have no built-in power supply can be made very small and they are therefore very easy to place where space is limited, for example. the stickers or skin.
Active tags, ARFID
Unlike passive tags are active tags, a separate power source that is used to send information and enforce its components. Communications from active tags to readers is much more reliable than communications from the passive tags. This thanks to active tags can create an active session with the reader. Active tags can also send the higher stress levels, thanks to their built-in power source, which facilitates the placement of such a man, because then the signal will pass through inhibiting materials such as liquids. The disadvantage is rather that they are much larger and more expensive to manufacture. Their range can extend up to several hundred meters and batteries are sitting in the can hold up to 10 years. It can also integrate more memory because the size is not as important.
Semi-Passive RFID
Is a mixture of passive and active tags where the big difference is that the integrated power source only operates micro-chip but not the actual transmission of signals. Advantages of this technique is that it is much more energy efficient and can, for example Login temperatures over a period and then present data on request from a reader.
The new CRFID
CRFIDs is too new to have ventured far from the lab yet. But it Juels says makes it possible to encrypt and decrypt data which could make chips in passports and credit cards more secure.
More on the University who are engaged in the development of CRFID can be found here: salajegheh-usenixsec09.pdf
VeriChip
With the emergence of micro-technology, some individuals have grown to fear of disqualification on grounds of RFID human implantation. VeriChip is working with an RFID implant, which will have GPS tracking capabilities.
This technique can not only track a single person, but every physical object that is, geographically located in each location and all times. Although this technique could provide assistance in locating missing children or the like, it also means the government to monitor everyone and everything that has RFID chip. Moreover Theoretically, this could be done without the knowledge or consent of the individual.
How can it look like?
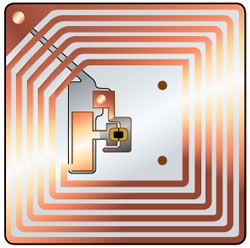
In practice, then?

What can RFID be used for?
If you understand the above, so you probably also understand the security risks of RFID. RFID can be used in many, many, and again in many areas. But what is perhaps the absolute worst thing is that people can easily become “infected” by RFID chips. They have even begun to advertise in the U.S. to bring these “tags” on children and animals in order to track all their movements and what they do. But RFID tags developed daily, and who knows what the future looks like. Right now you can at least use these tags to save vital information such as bank details, personal information, disease records, and much more
In what areas are used RFID technology?
RFID technology is of course of course its advantages, too. As that example to catch thieves in shops trying to take on products that are tagged.
But RFID technology offers great opportunities hospitals, where they can put a chip in a patient in order to check important information about their patients. Allowing doctors to treat their patients in a way from home. But all this is of course a disadvantage, too, that evil people
for example, could take over the patient’s chip, read journals and at worst might kill people, such as using Peacemaker as doctors steering away from home, even though I do not think that progress has been easy so far yet.
How is it developing?
Today’s RFID tags can only send fixed data back to a reader device, whether it’s information on your passport or of an endangered bird. The researchers are now working to import something very interesting to the tags in the form of microcomputers, which opens the way for much smarter applications.
Since RFID tags FREQUENCY shortage of batteries and cleans out all forces from broadcasting from its readers, makes limited power supply to the micro-computers a challenge. But it also has the advantage of being able to create the so-called computational RFID tags – CRFIDs – cheap, robust and long life.
What does all this then?
All this means a lot of fun opportunities. In all cases for me to find that extremely interesting. The advantage now is that RFID chips are very uncertain and do not even use any type of encryption to protect information found on the chip.
Here are some interesting youtube clips about the technology. Extra worth checking out is a myth buster when speaking at a conference on what happened when they thought of sending a section on how hackable these RFID chips are. Myth Buster clip:
https://youtu.be/X034R3yzDhw
Major Malfunction’ve been working with RFID and gave a presentation on it at Defcon :
References:
/wiki/Radio_frequency_identification
The SpyChips Threat by Katherine Albrecht & Liz McIntyre
Youtube.com
